What Is Encrypted Email? A Plain-English Guide to How It Works (and When to Use It)
Encrypted email protects the contents of your messages so only intended recipients can read them. This guide explains the basics in simple terms—what email encryption is, which methods exist (PGP and S/MIME), when to use it, and the limits you should be aware of.
What is “encrypted email”?
In plain terms, encrypted email is email that has been mathematically scrambled so that only someone with the correct key can read it. If anyone intercepts the message in transit—on public Wi-Fi, a mail server, or an ISP—they see gibberish. Once the intended recipient opens the email with their private key, the original text and attachments become readable.
It’s not new technology, but it’s become easier to use thanks to modern tools and privacy-first providers. If you send personal IDs, contracts, health data, or other sensitive information, encryption is a smart baseline—much like using seat belts in a car.
How email encryption works (quick, non-technical)
Behind the scenes, email encryption relies on public-key cryptography. Each person has a public key (shareable with others) and a private key (kept secret). When Alice wants to send Bob a confidential message:
- Alice looks up Bob’s public key.
- Her email app encrypts the message using Bob’s public key.
- Only Bob’s private key can unlock (decrypt) the message.
- Optionally, Alice can digitally sign the message with her private key. Bob verifies the signature to confirm identity and integrity.
The two main methods: PGP vs S/MIME
PGP (Pretty Good Privacy) / OpenPGP
PGP is an open standard widely supported across platforms. You create a key pair and share your public key. Others use it to encrypt messages to you; you use your private key to decrypt. PGP can be used with desktop clients (e.g., Thunderbird), browser extensions, or some privacy-focused webmail services. It’s very flexible and works even when organizations don’t have centralized control.
S/MIME (Secure/Multipurpose Internet Mail Extensions)
S/MIME uses X.509 certificates issued by a trusted certificate authority. Many enterprise email systems (Microsoft 365, Apple Mail) support S/MIME natively. It’s great for companies that can centrally issue and manage certificates for staff, with policies for revocation and renewal.
When should you use encrypted email?
- Sending sensitive data: IDs, contracts, financial or medical information.
- Discussing confidential business topics with clients or partners.
- Using risky networks: hotels, cafés, airports, or any place you don’t fully trust.
- Regulatory protection: Certain workflows benefit from encryption when aligning with privacy frameworks (e.g., GDPR).
What encrypted email does—and doesn’t—do
The following infographic summarizes the strengths and limits. Save or embed it in your post:
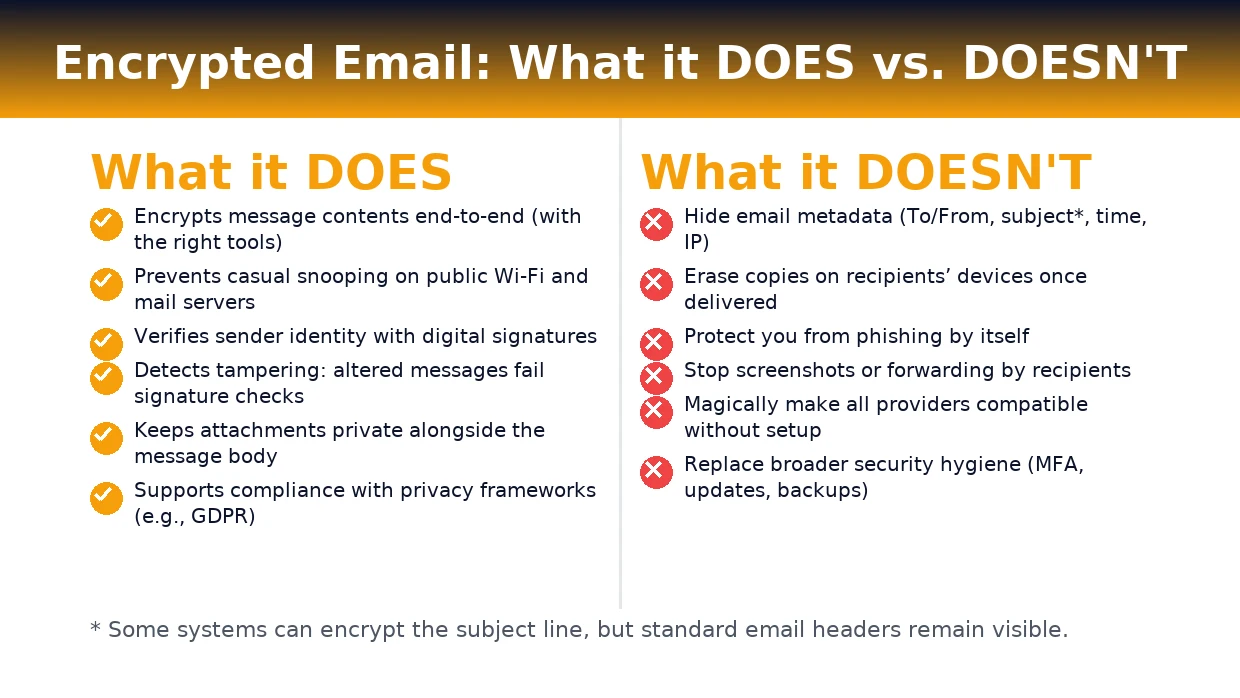
Key takeaways:
- Does: keep contents private, verify sender (with signatures), and detect tampering.
- Doesn’t: hide metadata, stop screenshots/forwarding, or replace good security practices.
How to set it up (practical paths)
Option A — Privacy-first email provider (easiest)
Several providers offer built-in encryption with automatic key exchange between users on the same service and simplified flows for outside recipients. This is the least technical approach for individuals.
Option B — Desktop mail client with PGP
- Install a mail client that supports OpenPGP (e.g., Thunderbird).
- Generate a key pair (public/private) and set a strong passphrase.
- Publish or share your public key (website, signature block, key servers).
- Import recipients’ public keys before you send encrypted messages to them.
- Enable “sign by default” for important conversations so recipients can verify you.
Option C — S/MIME certificates (great for organizations)
- Obtain S/MIME certificates for users from a trusted CA.
- Deploy via your organization’s management tools (MDM/Group Policy).
- Instruct staff to exchange and trust certificates for external contacts.
- Set policies for revocation (lost devices), renewal, and backup of keys.
Best practices & troubleshooting
- Use a passphrase manager: Protect your private key with a long, unique passphrase stored in a reputable password manager.
- Verify fingerprints: When exchanging public keys, verify the key fingerprint out-of-band (voice/video call) to prevent impersonation.
- Sign important emails: Even if you don’t encrypt everything, signing adds authenticity and tamper-evidence.
- Mind the subject line: Subjects are often visible; don’t put secrets there. Some tools can encrypt subjects, but interoperability varies.
- Attachments: Encrypt attachments alongside the message. If tools don’t handle it, zip and encrypt files separately before sending.
- Phishing still exists: Encryption won’t stop social engineering. Train yourself and your team to spot suspicious emails and enable MFA everywhere.
- Device security: If malware compromises a device, it can read decrypted content. Keep OS and apps updated and use reputable protection.
FAQ
Is encrypted email the same as “secure email”?
Secure email is a broad term. Encrypted email specifically means the message contents are cryptographically protected so only the intended recipient can read them. A “secure” email service may include other protections like strong authentication, spam/phishing filters, and zero-knowledge storage.
Can I encrypt email if the other person doesn’t use the same provider?
Yes, using standards like PGP or S/MIME. You’ll need the recipient’s public key/certificate. Some providers also support sending a secure link: the recipient authenticates via a one-time passcode to view the message in a web portal.
Does encryption hide who I’m emailing?
No. Standard email metadata (From/To, time, and usually subject) can remain visible. If you need stronger privacy for metadata, consider secure messaging apps that hide more of the envelope information.
What happens if I lose my private key?
You won’t be able to decrypt messages encrypted to that key. Keep encrypted backups of your private key and consider recovery mechanisms (organization key escrow, recovery codes) where appropriate.
Is end-to-end encryption compatible with search and spam filtering?
Server-side search and content-based spam filtering are limited on fully encrypted content. Some systems provide client-side indexing or hybrid approaches that balance privacy with usability.